What is Band’s VRF? (Whitepaper Digest Version)
Randomness is a fundamental function that helps to operate many modern decentralized applications (dApps). However, the root and foundation…

Randomness is a fundamental function that helps to operate many modern decentralized applications (dApps). However, the root and foundation of this vital randomness mechanism is often neglected. DApps often rely on “good” randomness that must be newly generated and independent of the state of the application. Essentially, random results should have integrity and must be verifiable, tamper-proof, and unpredictable.
For example, consider an online lottery system where participants place their bids, wait for the random result, and winnings are allocated according to the participant’s bid placements. Similarly, consider leadership elections (often used in committee-based blockchain platforms) that proceed in rounds to randomly elect a leader among the participants. With such applications or use-cases, it is crucial to guarantee that randomness is sampled uniformly and independently of the application’s state, therefore making it hard to predict as well as ensuring that there are no malicious actors who can affect the outcome of such lottery winnings and leadership elections.
Verifiable Random Function (VRF)
Applications that require “good” random values to be produced commonly rely on cryptography techniques to deliver pseudorandom values which are essentially values that are impossible to distinguish from uniformly randomized values. A Verifiable Random Function (VRF) is a mathematical operation that processes inputted values and generates a pseudorandom output along with the proof of authenticity of the output generation process. Challengers that question the random process can verify the proof to ensure that pseudorandom results are truly valid.
In general, the core of the VRF system will have a set of secret keys used to generate verifiable results and a set of corresponding public keys used to verify the results produced. For example, a secret key is generated in private, and a cryptographic function maps the seed to an output value along with its proof. The crucial property is that someone that does not have access to the secret key cannot distinguish, in polynomial time, the output from a value that is sampled uniformly at random from the range of all possible outcomes.
BandChain’s VRF Security Properties
- Unpredictability: This ensures that the computed outputs are distributed in a way that is, for all practical purposes, uniformly random. This is a fundamental property for VRF as it conveys that the VRF behaves in the same manner as a random oracle. In practice, this means that anyone without the secret key has no way of predicting the outcome in a manner that is better than “randomly guessing”, even when the seed is known.
- Uniqueness: This ensures that after the VRF providers publish their secret key, the providers can only produce proof that helps to verify the authenticity of the VRF output value for every seed. In other words, for a given secret key and seed, it is incredibly difficult to find two different VRF values that both pass the verification. This property is crucial to protecting against malicious actors that try to claim a specific output that is generated in a manner that violates the intended purpose and objective.
- Collision-Resistance: This ensures that it is computationally difficult to find two different inputs such as “seed1” and “seed2”, that have the same secret key to obtain the identical output value — similar to the classic property of the cryptographic hash function. The difference for VRFs is that the property remains to be true even against an adversary that knows the secret key. This offers a different type of protection than that from its unique property. For example, it protects against a party that tries to claim an output that is computed from, say input “seed1” as if it was computed from a different, say input “seed2”.
What is BandChain’s VRF?
Our solution for verifiable pseudorandomness is based on the BandChain blockchain. Our protocol uses a Verifiable Random Function (VRF) to cryptographically secure and verify that produced results have not been tampered with.
BandChain Verifiable Randomness extends the general form of the VRF system to serve requests from dApps, based on the distributed BandChain Oracle Network. BandChain is a public blockchain that provides APIs for data and services that are stored “off-chain” on the traditional web or from third-party providers. It supports generic data requests from other public blockchains and performs on-chain aggregation according to the BandChain Oracle Scripts. The aggregation process works like a smart contract on the EVM platform as the process is executed on-chain and an oracle result is produced. The oracle results are also stored on the BandChain.
After that, the results will be sent to the calling dApp on the main blockchain (typically Ethereum or other EVMs), along with a proof of authenticity via customized one-way bridges or via Inter-blockchain Communication Protocol. To guarantee verifiable “good” randomness that is suitable for security-critical applications, we deploy the cryptographic primitive of Verifiable Random Functions. Band’s VRF provides values that are indistinguishable from uniformly random generated values, with the added benefit of having a verified proof of authenticity that concerns the pre-published public key.
Protocol Flow
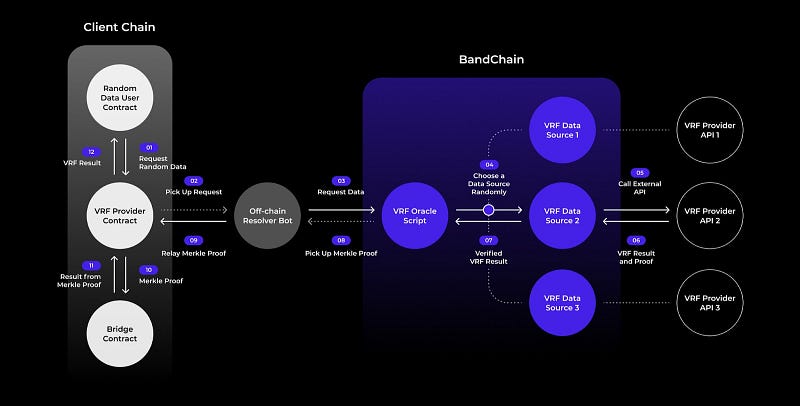
At a high level, our protocol works as follows.
- First, two contracts, the VRF contract and the Bridge contract, are deployed on the main chain (Ethereum or other EVMs). The first contract is responsible for receiving randomness requests from dApps and it contains code that pre-processes the request to be ready for submission to the Band side-chain. It also works as the receiving end of the request’s result. The second contract, as the name denotes, works as the connecting “bridge” between the two chains to validate the latest state of the side chain and verify that the received results from VRF requests are indeed the ones computed and stored on the BandChain.
- A third-party dApp that wishes to request a random value, submits its request to the VRF contract, which then prepares the actual VRF input by expanding it into a VRF seed. This is then picked up by incentivized actors and/or the Band Foundation and is submitted as a VRF request to the BandChain.
- In particular, a VRF Oracle Script collects this request and then maps it to the set of VRF data sources that are available to the chain, as well as a number of BandChain validators. The Oracle Script then randomly assigns the request to a VRF provider that corresponds to one of the VRF data sources. The assigned provider evaluates the VRF based on the prescribed input using its VRF secret key and then broadcasts the result to the Band Network.
- After that, all chosen validators run the VRF verification algorithm using the assigned provider’s public key and if the verification is successful, the result will be transmitted to the VRF Oracle Script. After collecting the necessary number of results from the validators, the Oracle Script will accept the majority as the final result which then becomes part of the BandChain state.
- The final result, which will be included in next block’s computation, is sent back to the main chain’s VRF contract with a Merkle tree proof for its inclusion on the BandChain’s state. Finally, this proof is verified with the Bridge contract and after a successful check, is sent to the original dApp.
To learn more about Band’s VRF, visit these official channels:
- VRF Landing Page: https://bandprotocol.com/vrf
- VRF Whitepaper: /content/files/static/band-vrf-whitepaper.pdf
- Example Use-Cases: https://docs.bandchain.org/vrf/example.html
- How does Band VRF works?: https://docs.bandchain.org/vrf/introduction.html
Follow Band Protocol to stay up to date on our latest updates:
Twitter | Telegram | Medium | Youtube | Discord | Reddit | Github



